What is Privacy? There are many different definitions of “privacy.” We are going to focus on personal privacy, protecting the information about you that others collect. In today’s digital world, you would be astounded at all the different entities that not only collect information about you, but who then legally share or sell that information. […]

LOYOLA UNIVERSITY CHICAGO • March 1, 2026
Loyola Information Security Blog
University Information Security Office
Search
Recent Post
- February 2026 Newsletter: Electronic Gift card Scams are on the rise
- Happy New Year from UISO: Set a Cyber Resolution for 2026
- MFA – Why it matters
- October is National Cybersecurity Awareness Month
- Watch out for “E-Signature” Phishing Scams
Archives
- February 2026
- January 2026
- November 2025
- October 2025
- September 2025
- August 2025
- July 2025
- June 2025
- April 2025
- March 2025
- February 2025
- October 2024
- September 2024
- August 2024
- July 2024
- June 2024
- February 2024
- January 2024
- November 2023
- October 2023
- August 2023
- July 2023
- June 2023
- May 2023
- March 2023
- February 2023
- January 2023
- November 2022
- October 2022
- September 2022
- August 2022
- May 2022
- March 2022
- February 2022
- January 2022
- December 2021
- November 2021
- October 2021
- September 2021
- August 2021
- July 2021
- June 2021
- May 2021
- April 2021
- March 2021
- February 2021
- January 2021
- December 2020
- November 2020
- October 2020
- August 2020
- July 2020
- June 2020
- May 2020
- April 2020
- March 2020
- February 2020
- January 2020
- November 2019
- October 2019
- September 2019
- August 2019
- July 2019
- June 2019
- May 2019
- April 2019
- March 2019
- February 2019
- January 2019
- December 2018
- November 2018
- October 2018
- September 2018
- August 2018
- July 2018
- June 2018
- May 2018
- April 2018
- March 2018
- February 2018
- January 2018
- December 2017
- November 2017
- October 2017
- September 2017
- August 2017
- July 2017
- June 2017
- May 2017
- April 2017
- March 2017
- November 2016
- October 2016
- September 2016
- August 2016
- July 2016
- June 2016
- May 2016
- April 2016
- March 2016
- February 2016
- January 2016
- November 2015
- October 2015
- September 2015
- August 2015
- July 2015
- June 2015
- May 2015
- April 2015
- March 2015
- February 2015
- January 2015
- December 2014
- November 2014
- October 2014
- September 2014
- August 2014
- July 2014
- June 2014
- May 2014
- April 2014
- March 2014
- February 2014
- January 2014
- December 2013
- November 2013
- October 2013
- September 2013
- August 2013
- April 2013
Mykael Baig
Phishing Scam – “Process Has Begun By Our Administrator To Upgrade Your Account” – April 14, 2021
April 22nd, 2021
Below is the most recent phishing email and website we have seen. Similar to past emails, this scam attempts to trick users into entering personal account information (e.g. username/password). Users should not click any links in this email and should delete it right away. As a reminder, Loyola will never ask for your password or […]
Potential Risk for Gmail Users On iOS Devices
July 14th, 2014
What It Is A vulnerability has been reported for Google’s Gmail iOS app that would allow for an attacker to intercept all email communications through a Man-in-the-Middle (MitM) attack. The MitM attack allows a third party to intercept your data before it is received by the designated recipient. Additionally, if an attacker can trick your device into […]
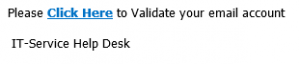
November 11, 2014 Phishing Report
November 11th, 2014
Over the past week or so, the UISO has noticed an increased amount of these phishing e-mails, stating that the receiver’s password is about to expire, and they need to validate his or her e-mail account. These e-mails are coming from seemingly random senders, and not from within Loyola’s network, as you can see by their […]
December Edition of OUCH!: Anti-virus
December 4th, 2014
SANS has released their December edition of OUCH!, covering the functions and limitations of anti-virus. “We are excited to announce the December issue of OUCH! This month, led by Guest Editor Jake Williams, we explain what anti-virus is, how it works and its limitations. Ultimately, our goal is for people to understand that while anti-virus helps […]
January Edition of OUCH!: Mobile Apps
January 14th, 2015
SANS has released their January edition of OUCH!, covering how to securely use mobile apps. “We are excited to announce the January issue of OUCH! This month, led by Guest Editor Chris Crowley, we cover how to securely use mobile apps. Since many of you have new mobile devices after the holidays, we figured this was a perfect time […]

University Employee Payroll Scam
January 15th, 2015
Earlier this week the Internet Crime Complaint Center (IC3) and FBI sent out a report regarding a phishing scam targeting university employees. Users are receiving e-mails about a change in their human resource status and are sent to a link to website to address this change. The link sends the victims to a page that looks […]

January 15, 2015 Phishing Report
January 15th, 2015
Recently the Information Security Office has noticed many instances of a phishing scam requesting users to download a document from Drop-Box for their financial records. The e-mail contains many different sections that may seem legitimate, but you should NOT open the link or respond to the e-mail. Please note that the download link in the body […]
February Edition of OUCH!: Staying Secure on the Road
February 5th, 2015
SANS has released their February edition of OUCH!, covering “how to securely stay online and get work done while traveling.” “We are excited to announce the February issue of OUCH! This month, led by Guest Editor Steve Armstrong, we cover how to securely stay online and get work done while traveling. With more and more people […]
March 17, 2015 Phishing Report
March 17th, 2015
Over the past several weeks, the Help Desk and Information Security Office have received complaints of numerous spam e-mails claiming that “Your e-mail account was LOGIN today by Unknown IP address:”. The subject line is generally “Support” and the e-mail instructs the user to “click on the Administrator link below and LOGIN”, which then provides a bogus link […]