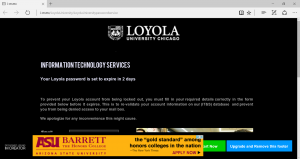
Several Loyola staff and faculty have received an email that appears to be from a Loyola email address requesting that they change their password. The link in the email will open to a page that looks to be an official Password Change page from the university. Although this page is not in the normal Loyola […]

LOYOLA UNIVERSITY CHICAGO • March 1, 2026
Loyola Information Security Blog
University Information Security Office
Search
Recent Post
- February 2026 Newsletter: Electronic Gift card Scams are on the rise
- Happy New Year from UISO: Set a Cyber Resolution for 2026
- MFA – Why it matters
- October is National Cybersecurity Awareness Month
- Watch out for “E-Signature” Phishing Scams
Archives
- February 2026
- January 2026
- November 2025
- October 2025
- September 2025
- August 2025
- July 2025
- June 2025
- April 2025
- March 2025
- February 2025
- October 2024
- September 2024
- August 2024
- July 2024
- June 2024
- February 2024
- January 2024
- November 2023
- October 2023
- August 2023
- July 2023
- June 2023
- May 2023
- March 2023
- February 2023
- January 2023
- November 2022
- October 2022
- September 2022
- August 2022
- May 2022
- March 2022
- February 2022
- January 2022
- December 2021
- November 2021
- October 2021
- September 2021
- August 2021
- July 2021
- June 2021
- May 2021
- April 2021
- March 2021
- February 2021
- January 2021
- December 2020
- November 2020
- October 2020
- August 2020
- July 2020
- June 2020
- May 2020
- April 2020
- March 2020
- February 2020
- January 2020
- November 2019
- October 2019
- September 2019
- August 2019
- July 2019
- June 2019
- May 2019
- April 2019
- March 2019
- February 2019
- January 2019
- December 2018
- November 2018
- October 2018
- September 2018
- August 2018
- July 2018
- June 2018
- May 2018
- April 2018
- March 2018
- February 2018
- January 2018
- December 2017
- November 2017
- October 2017
- September 2017
- August 2017
- July 2017
- June 2017
- May 2017
- April 2017
- March 2017
- November 2016
- October 2016
- September 2016
- August 2016
- July 2016
- June 2016
- May 2016
- April 2016
- March 2016
- February 2016
- January 2016
- November 2015
- October 2015
- September 2015
- August 2015
- July 2015
- June 2015
- May 2015
- April 2015
- March 2015
- February 2015
- January 2015
- December 2014
- November 2014
- October 2014
- September 2014
- August 2014
- July 2014
- June 2014
- May 2014
- April 2014
- March 2014
- February 2014
- January 2014
- December 2013
- November 2013
- October 2013
- September 2013
- August 2013
- April 2013
Jim Pardonek
SPAM Email Contains Ransomware
April 7th, 2016
Early this morning, Loyola email users may have noticed an email in their inbox that appears ot come from a legitimate source containing a Word document that has an embedded program that attempts to install ransomware named “Locky” The email looks to be from: ebilling@angelsprings.com and has the subject line: “Your Latest Documents from Angel […]
Thursday May 5th is World Password Day
May 5th, 2016
May 5 is World Password Day, an annual effort to encourage safe password practices. The World Password Day 2016 theme is multi-factor authentication (MFA) – also called two-factor authentication (2FA) or two-step verification – which provides an extra layer of security to your online activities. The National Cyber Security Alliance (NCSA), a proud champion […]
JavaScript Ransomware Spreading
January 6th, 2016
What is believed to be the first JavaScript-based ransomware-as-service is spreading. Because of the way it works, Called Ransom32, it is likely to be able to infect multiple operating systems including Windows Mac and Linux. It is generally spread via phishing type email and is contained in a self executing ZIP file attachment that is […]
Welcome to National Cyber Security Awareness Month
October 8th, 2015
October is National Cyber Security Awareness Month (NCSAM), conducted every October since 2004, this national public awareness campaign is intended to encourage everyone to protect their computers and our nation’s critical cyber infrastructure. Cyber security requires vigilance 365 days per year. However, the Department of Homeland Security (DHS), the National Cyber Security Alliance (NCSA), and […]
August 23, 2013 Phishing Report
August 23rd, 2013
This one was captured this morning. Luckily there are no links in this one. From: Sung Lee Sent: Thursday, August 22, 2013 5:07 PM To: Recipients Subject: Business Ethics. Greetings, I am Mr.Sung Lee,Auditing and Account Credit Officer,Dah Sing Bank Ltd (Hong Kong).I will give you the details but in summary,the funds are coming via […]
August 26, 2013 Phising Report
August 26th, 2013
This is the latest phishing email reported to the Loyola Information Security Office From: LUC-Webmaster [mailto:webteam@luc.edu] Sent: Tuesday, August 27, 2013 11:35 AM To: WebTeam Subject: Update Dear User Your password will expire in Three Days Click on the link below to validate your e-mail. CLICK HERE System Administrator The link is an attempt to […]
August 22, 2013 Phishing Report
August 22nd, 2013
After a quiet few days, the phishers are at it again. The first one from today was easy to identify because it came from a London bank: Our Valued Account Holder, Lloyds TSB Bank technical services department is carrying out a scheduled software upgrade to improve the quality of services for the online banking customers. […]
August 15, 2013 Phishing Report
August 15th, 2013
This phish was received by one of our automated mailboxes this morning. It claims that your account has been compromised and unless you follow the instructions, your account will be blocked. ATTENTION : MAIL VIOLATION NOTIFICATION This Account has been Compromise; User is advice to follow the admin assistance below for authentication of this account. […]
It’s IRS SPAM Season Again
April 11th, 2013
As we get closer to the tax filing deadline, many of us have received or are anticipating a refund (at least we hope so). Spammers, looking to make a quick buck, sometimes hundreds of dollars, use this opportune time to send messages aimed at getting one’s personal information and thus access the one’s bank account. […]