Last week, security researchers identified a new ransomware trojan in the wild. This new variant, deemed ZeroLocker, operates in a similar fashion to last year’s CryptoLocker. Ransomware is a category of malware that restricts access to a computer or files and demands a ransom be paid to restore access. CryptoLocker and ZeroLocker accomplish this by encrypting files and not releasing the encryption key or decryption program until the ransom is paid.
A key difference between CryptoLocker and ZeroLocker is the latter encrypts ALL files on the computer except those in folders that are required for the computer to run or files larger than 20 megabytes. This means uncommon files are included in the encryption process in addition to photos, documents, and videos.
At the time of this writing, researchers have also determined that ZeroLocker may have a fatal bug in its programming. After the malware is installed, the program generates a unique key to encrypt files. This key should then be stored on a central server that is controlled by the attacker. However, it appears that this storage process may not actually be successful. This means, even if the ransom is paid, you may not be able to decrypt your files. (Source: http://www.scmagazine.com/errors-in-zerolocker-means-paying-ransom-may-not-decrypt-files/article/367593/)
Below is a screenshot of the program after encryption has occurred:
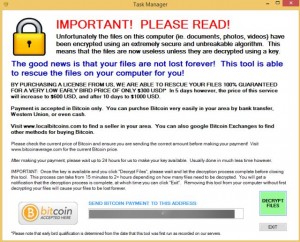
ZeroLocker was discovered by security researchers only a few weeks ago. Therefore, more in-depth information on the program is not available at this time.
The University Information Security Office has put protection in place to help prevent computers from being infected, however, you should be extra cautious when clicking links in emails and websites. If you suspect your computer has been infected, please contact the LUC Helpdesk at helpdesk@luc.edu or 773-508-4444.
